Nine key points about embedded system security that need to be understood before product design
Embedded systems are the heart and soul of the Internet of Things (loT), and they have been widely used in our lives, from home cars to small medical pacemakers. Usually embedded systems are designed to perform specialized functions with lightweight operating systems and software in the form of firmware.
Since many widgets and machines driven by embedded devices must be connected to the Internet during operation, network hackers have the opportunity to steal access, run malicious code, and attack connected components or even entire systems in the process. Embedded devices have become a major target for hackers.

It is particularly important to protect the security of embedded systems.
We often hear about the hacking of important computer systems, compared to the security of embedded systems, which is often overlooked.
The risk is real
Back in 2015, car company Fiat Chrysler recalled 1.4 million vehicles due to safety concerns. Two technicians wirelessly hacked into a Jeep through the dashboard connection system. They took control of not only the radio and air conditioning, but also the core functions of the car’s engine, brakes and steering. The incident revealed the potential for hacking to cause a substantial crash of a car and served as a wake-up call to automakers.
In 2021, academics at the University of Virginia and the University of California, San Diego, discovered a new variant of the phantom exploit that is expected to affect billions of computers. It can bypass all current protections against the phantom vulnerability on Intel and AMD processors and can take out virtually any device in one fell swoop, including desktops, laptops, cloud servers and smartphones.
Why is security for embedded systems different?
Embedded systems typically use the same design module to produce a large number of devices. Looking back at our previous cases, the number of embedded systems found in cars, cloud servers, and cell phones is in the tens of millions, with security vulnerabilities in a single system presenting millions of opportunities for hackers to attack.
Compounding the problem is the market’s need for speed in product development. In the fast-moving technology market, product design time is constantly compressed, and the emphasis on functionality sometimes outweighs security.
In the absence of protection against malicious hackers, an attack on a product can result in reputational damage to a company and affect long-term profitability and growth.
Nine key points to understand before designing an embedded system
Make a good mental preconception: the product may become the target of hackers
Even the best designers can slip up on a car’s premium audio system. Before 2015, would anyone have thought that cars could be hacked through some remote device? Probably not, but once one understands how computer systems control these steel and electronics, it makes sense.
Every device in the system needs to be protected, and as with the previous automaker case, it only takes one vulnerability to affect the performance of an entire complex system.
2.”Embedded systems are hard to attack” ?
This has been proven wrong countless times, and because a large number of devices all run the same system, a single intrusion can lead to thousands of hacking attacks.
When an embedded device is not secured, it is extremely vulnerable to hacking every time the device is deployed. Hackers will focus their attacks on the installation before using the device. However, when the embedded device has secure hardware or algorithms with personalized passwords, this threat is greatly reduced or even eliminated.
3.The system may not be completely protected from attacks by passwords and encryption
Password protection depends on the efforts of the user. However, according to a survey by Nordpass, a cybersecurity company, the most commonly used password in 2021 will still be “123456”, with millions of people coincidentally choosing the same password combination.
The top 50 passwords on the list of most commonly used passwords can be cracked in less than one second. Hackers may have their “work” covertly implanted in embedded devices. Malware is a ticking time bomb that can be activated at any time later.
While many users change their passwords when warned of a potential threat, embedded devices can still be compromised. Given this, a security solution to protect embedded devices would greatly improve the overall security of the system.
4.The cost of embedded security solutions is not high compared to addressing risks after the fact
Many companies do not have safety experts in their product design departments, and hiring outside consultants can cost more than $1,000 per hour, but the cost of an embedded safety solution is not prohibitive when compared to the cost of the 1.3 million vehicle recall, or the cost of litigation, involved in the case mentioned earlier.
Using the analogy of safety and security in public swimming pools: pools are designed for safety, including fenced perimeters, non-slip mats, and lifeguards. Most of these features are unobtrusive, but they are very effective for safety and security at a moderate cost.
Pools do not require a 30-foot high fence or hundreds of lifeguards or armed guards to enforce no-running requirements around the pool.
The real solution is to choose the right security guarantee based on the application scenario.
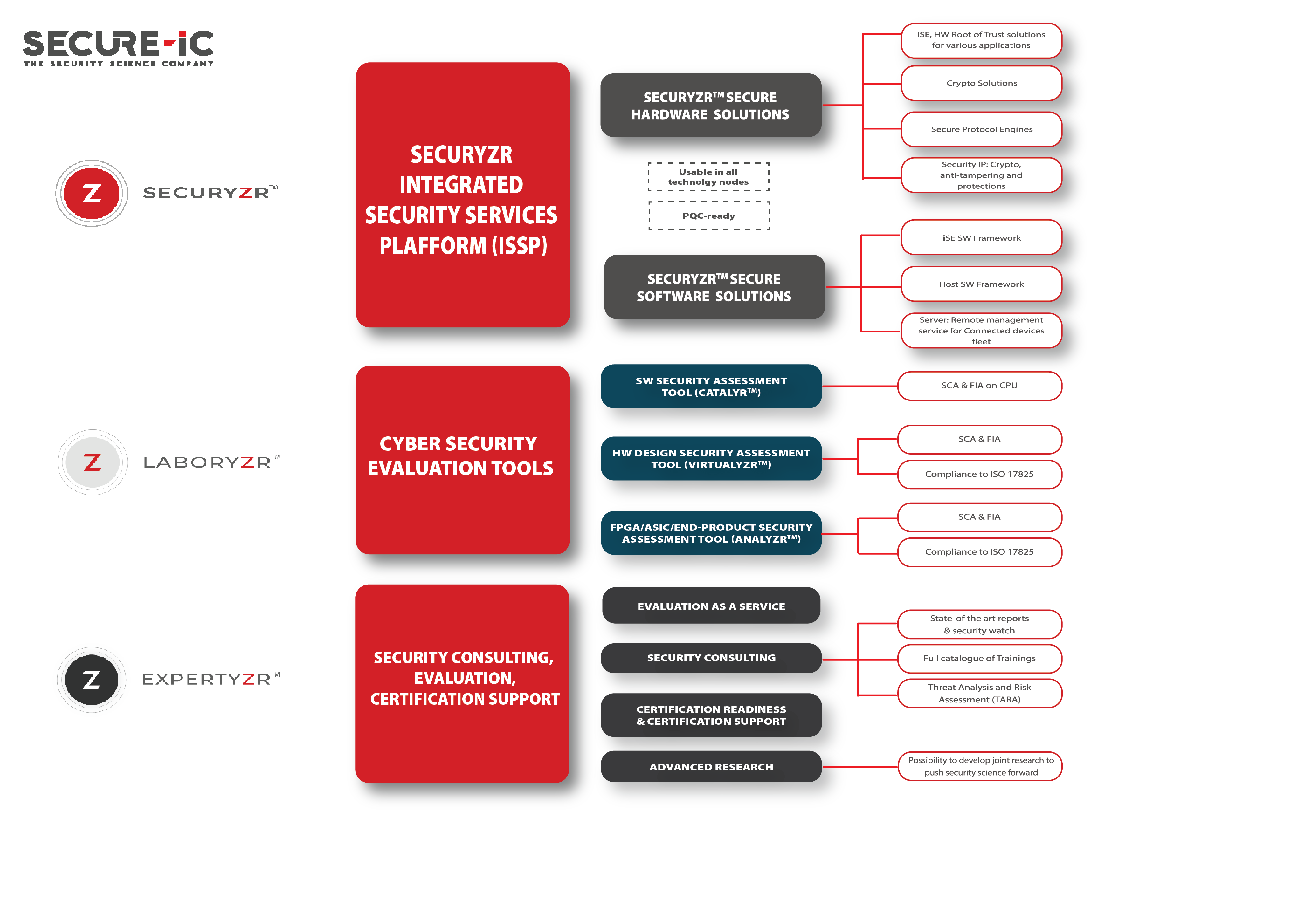
Secure-IC provides solutions for a wide range of applications in the following scenarios.
5.It is difficult to add security in the late stage of product development
In most cases, security assurances are included in the company’s plan. However, in the early stages of product development, security may be considered last due to lack of funds, and some design teams may intend to add security to the product later. The reality is that it is very difficult, if not impossible, to add security at the end of the development cycle.
The formation of a security solution requires thoughtful consideration. At the beginning of the development cycle, developers need to conduct security analysis and considerations. Experts recommend that development teams assess system assets and threats at the beginning of a project and consider security issues before starting any development or coding.
The advantage of considering security in the planning phase is that security requirements can be generated accordingly to the system objectives. The process will also build a system environment that can protect assets from security threats. The team can also more effectively select the hardware and software needed to achieve the security goals.
Launching a security program at the end of the development cycle can result in selecting the wrong hardware and software, which means either redoing a complete system or accepting a less secure solution.
6.Power consumption is no longer a key issue affecting the security of the security
The power consumption of embedded devices was once seen as a critical issue. Development teams needed to extend battery life and reduce the impact of the system on the environment. In the past this issue was primarily hardware driven, but advances in hardware design and the use of hardware gas pedals and special function blocks have changed this; in today’s embedded systems, software plays an increasingly important role in energy management requirements.
Energy consumption can be reduced by shutting down some operations when not in use, which reduces the power required on the hardware and software side, and it is critical to consider the need to disable certain security for a period of time.
As an example: once the device has finished booting, the boot security algorithm may then be turned off. Or the security features for peripheral communication may be disabled when there is no communication with inputs and outputs. Using these strategies, the power consumption for security is typically reduced to less than 5% of the total energy consumption.
7.Pay attention to potential threats
During product development, most people are so focused on creating a robust and functional system that it is easy to overlook risk issues such as understanding security threats.
If the development team overlooks the critical step of assessing threats early in the design process and fails to identify security alerts, irreversible consequences can result. If for some reason the design team lacks the relevant expertise, a brief consultation with a security expert is a good option.
8.Safety issues cannot be taken for granted
Since the advent of security measures for embedded systems, many have argued that adding AES encryption to embedded systems would meet all their security needs. AES encryption (especially at the 128- and 256-bit algorithm levels) does provide strong protection against Brute Force Attacks, which have been calculated to take over a billion years to break passwords using random numbers.
However brute force cracking is not the only threat, security personnel have other issues to consider, such as looking at the chain of trust for events and activities.
9.Pre-made third-party security chips will not work perfectly for all applications
While a third-party silicon solution is better than no security, it is a “one-size-fits-all” solution. Just as there is no one-size-fits-all hat, this solution is only suitable for general applications.
Secure-IC can custom develop a security solution that fits your needs perfectly.
Security is the foundation of embedded system design
Development teams often work under time constraints and need to get products to market quickly to stay ahead of the competition. The requirement to add more functionality adds even more pressure on the team in the midst of tight deadlines. Designing without a reliable embedded security solution is likely to lead the team into a situation where they end up redesigning again.
Experience has shown that security is as important as new features in the long run, and it can be very costly to find out at the last minute that a redo or even a redesign is needed.
Security is the foundation of embedded system design.
Secure-IC offers a variety of modules to create a solid security foundation for you