1 Awareness of MCU security needs to be cultivated
Today’s IoT devices face many different security issues than in the past, so ST has strengthened its investment in security. 2015 before and after, ST’s security chip and MCU (microcontroller) platform belong to the same large department, because it was found that hackers have not only attacked high security applications, such as bank cards, ID cards, etc., but has gradually expanded to the public level. For example, four or five years ago there were already smart speakers and smart videos for smart homes that were breached, and many customers gradually discovered that the threat of security risks could bring down the entire network, and there were even some vendors held hostage to blackmail by hackers.

Traditional MCUs already have some security capability, unfortunately there are many embedded developers who don’t pay much attention to security issues or don’t have the relevant knowledge and ability to enhance security, so ST has been gradually cultivating this market and educating customers in the past four to five years.
As the use of IoT fragmentation devices is becoming more and more widespread, people do not know from which weakest link hackers will enter, so extra enhance the security of the MCU.
2 How the STM32WL LoRa wireless system-on-chip ensures security
At the end of 2020, ST launched the STM32WL LoRa wireless system-on-chip family for the mass market, with the WL5 in a dual-core form factor, adding M0+ cores in addition to the M4 cores, with the benefit of upgrading some applications that require higher security in the same system, i.e., a great help to customers in terms of security upgrades; in addition, advanced security features have been added.
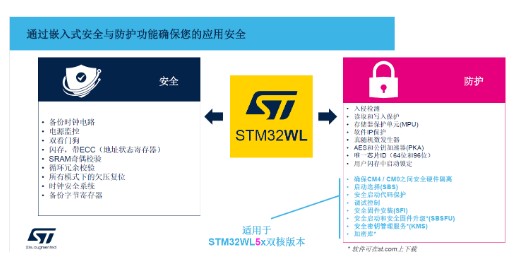
Figure 1 Security and Protection of STM32WL
Specifically, the STM32WL is based on a number of upgrades to the legacy STM32 platform. In fact, due security is already available on the existing STM32, as shown in Figure 1, with black font depicting the security facilities that are available on the existing STM32 product line, such as power monitoring, flash protection, clock security, intrusion monitoring, software IP, etc., which are all supported by the existing STM32.
On top of that, the dual core can provide higher security features including hardware isolation for M4 and M0+ security, secure boot code protection, etc. And, when adding these higher security dual-core hardware versions, ST’s customer base can quickly upgrade from existing platforms, guiding developers to quickly embed security concepts into the design framework of their products.
For developers, dual-core places particular emphasis on four key features: data encryption, secure download, firmware protection and authentication. These 4 key security features were selected by ST during its interaction with developers over the past decade in product security design and development and are considered to be the main keys to solve developers’ pain points.
1) Data Encryption
Data encryption drives the Secure Key Management Service KMS system, which means that a special secure domain is provided in the chip to store keys to manage the use of different applications in the system, and also to handle privileges, which were not available in traditional general-purpose MCUs in the past.
2) Firmware IP protection
Many of our customers are developing hardware firmware to execute applications on the chip, and many of them are very worried about their products and the IP in the firmware being stolen, breached, and stolen by hackers. So there is a secure boot (trusted root) in WL5 for them to use and protect the firmware with more confidence. There are some specific domains in which only these applications can be executed after they have been authenticated in these firmware memories.
3) Secure firmware installation and update
In the implementation process, more and more IoT devices of all kinds of upgrade requirements must continue to happen, that is, the user may have to do code updates, firmware updates in the process, which is very difficult to do in the current environment, but also more time-consuming, labor-intensive and resource-intensive. Once many devices are available, it is difficult to do firmware updates, which increases the difficulty of maintaining the whole ecology.
For this reason, WL5 has 2 features: (i) Embedded Secure Firmware Installation (SFI); and (ii) SBSFU, which gives a definable field update on top of that to perform secure platform upgrades. In addition to these 2 firmware, ST also provides reference code to support users to use it more quickly and allow them to better implement this feature.
4) Encryption / Password
These foundations must be embedded in cryptographic and encryption modules with strong security. For example, ST has a relatively strong hardware encryption coprocessor that adds digital signatures to ensure that existing MCUs can achieve encryption functionality and capabilities even with limited resources.
When it comes to the most important existing customers, when doing application development firmware upgrades, they know about secure boot and chain of trust, and the idea of chain of trust is not the latest, but really implemented on the MCU in recent years. There needs to be a mechanism on the chip for these chips to have to perform a secure boot at the beginning of the execution or at reset. Under the secure boot mechanism, the chip checks itself to see if the registers or peripherals on the chip have been tampered with. Under these measures, it will go through step 2 to authenticate whether these applications are allowed to certify its legitimacy, and if these are normal, then this application can only start in a specific domain, which will greatly reduce the destructibility or errors, or give hackers the opportunity to intercept or crash the whole system. So the root of trust is an extremely important part of security conception. ST is also constantly nurturing developers, engineers, and going faster to improve their security concepts.
Thanks to ST’s dual-core push, these application advantages, such as SFI, SBSFU and also KMS, can bring out the best in applications while maintaining maximum flexibility. Features that were previously not available or more difficult, or required high cost and capability to implement, can now be more convenient and easier for developers to implement.
The following five points are very important for any IoT device: ① developers need to have the flexibility to implement different levels of security, because the device itself protects different levels of data, and it is impossible to spend a lot of money to protect it with only very rudimentary security features; ② about IP protection, as more and more developers implement different features, performance in their middleware or firmware, these IP protections will It is very important to have a better way to protect their IP. The next three are upgrades related to device replicability, attackability, and trustworthiness, which are necessary features for future IoT devices and will be well established and easily available to developers.
3 MCU full lifecycle security management
In the whole chip development process, the security lifecycle includes the design, flow, test, and test tools after the chip is given to the developer. If it is attacked, it will reset or erase all the code on the flash memory to a certain extent, which is the aspect that ST MCU can handle at present.
In the latter part of the life cycle, the heaviest aspect is self-destruction. This can be available in a secure chip, but there is no similar functionality in a traditional MCU yet, depending on whether the developer wants to build this into their development or lifecycle management.
4 Security has multiple paths
If Arm TrustZone is good, why is TrustZone not used in the STM32WL LoRa wireless system-on-chip?
In fact, the TrustZone concept was originally proposed by Arm as the most basic idea of code isolation or security isolation for implementing security features. In the past ten years, TrustZone has been recognized in different security chips, and many manufacturers have put TrustZone STM32 general-purpose MCU used to use M-core, which is not TrustZone, so on the basis of Cortex-M, if you want to implement similar TrustZone-M, it is necessary to implement the hardware physical isolation. If the hardware is physically isolated, it is necessary to take a different approach, which is based on the dual-core design concept, and implant the TrustZone concept (not TrustZone itself) into the traditional general-purpose MCU.
As you can see, there are many ways to achieve security, and TrustZone is only one of them. In addition, there are firewalls, proprietary code read protection (PCROP), as well as unique boot entry, BootLock, and user secure storage, etc. The STM32 has a range of security-related hardware, combined with dual cores, and others that are not dual cores, that can achieve or meet the level of security required by customers.
